D Do no access 2. Each of the following is true about privacy EXCEPT.

I Had Applied For A Posting In Infosys And Got The Following Whatsapp Message From Them I Responded Yes But I Have Not Received Any Mail From Them Is There Something I
A small program that gets installed on a computer while browsing the Internet.

. Thus the correct option is d. Reusing the same password across multiple sites is a good idea. But many leaders are not sure where to start.
GDPR applies to which types of individuals or organizations. B overloading of transport-layer mechanisms. After three years fathers age will be ten years more than twice the sons age.
Weak or non-existent mechanisms for authentication is an example of session layer vulnerability. Infosys Questions with Answers. Here are 20 important data privacy questions your team can start reviewing now to build a strong data privacy and security practice.
Security is a process. If your password is stolen in a hack of 1 site user can use that to gain acces to your accounts on other sites. Adone is attempting to explain to his friend the relationship between security and convenience.
It has only just recently become a concern. Rule et al 1980. Companies like Microsoft Intel and Lucent Technologies had to block their Internet connections due to its action.
The basic function of active content is to provide an interactive Internet experience through videos and toolbars. D Blood group is sensitive information 4. Sometimes active content is used to gain unauthorized access to a computer and then damage the data stored on it or.
Privacy is the ability of an individual or group to seclude themselves or information about themselves and thereby express themselves selectively. Distance travelled by plane 110 distance travelled by ship 180. PRIVACY DATA PROTECTION 1.
C poor handling of unexpected input. It sure is convenient but this convenience comes with a price. Privacy Policy Many organizations have a privacy policy to deal with the growing privacy concerns of the customers.
Now x-4 x-4 x-4. Equation is 3x-12 x. What is the fathers present age.
All data controllers and processors established in the EU and organizations that target EU resident. Each tree has a high variance with low bias. But trusteeship at Infosys goes further than that.
Citizens have a right to privacy based upon the US. Supreme Court has said that the US. After it had travelled 180 miles a plane statrted with 10 times the speed of the ship.
A weak or non-existent mechanisms for authentication. D highly complex application security controls. A ship went on a voyage.
There is no maximum fine. Data privacy and information security can be daunting and their teams are already overwhelmed. Is the following statement true or false.
D All of the above 5. Business process redesign 2. The company was founded in Pune and is headquartered in Bangalore.
Option A Solution By Examveda Team Privacy is a moral right to be left alone. Trusteeship also includes our corporate commitment to utilizing natural resources in a sustainable way and to improving the communities in which we live and work. Infosys Limited is an Indian multinational information technology company that provides business consulting information technology and outsourcing services.
Only corporations and government need to be concerned about it. Collaboration and partnership 5 A task of developing a technical blueprint and specifications for a solution that fulfills the. Dhanoop Bhaskar June 19 2009 aptitude.
Personal info not be protected. 1We build the N regression with N bootstrap sample. Multiple Choice The US Supreme Court has said that the US.
Scholars from diverse backgrounds in history sociology and political science have all concluded that the existing set of privacy laws do not in fact protect privacy well and that privacy law is far behind the developmental trajectory of information technology PPSC 1977. The risk of not securing data and protecting privacy is too great. The boundaries and content of what is considered private differ among cultures and individuals.
Which of the following statements about privacy is true. 116 Which of the following is true regarding privacy rights. Scanned copy of passport.
Privacy is the right to be left alone to the degree that you choose. Security and privacy 5. Knowledge asset management 3.
4 Which one of the following is not a business driver for an information system. 2We take the average the of N regression tree. Saved Which of the following is true regarding privacy rights.
Security includes the necessary steps to protect from harm. Any organization that processes personal data. Privacy is freedom from attention observation or interference based on your decision.
Blood group of Infosys Colleague. It is termed as Personally Identifiable Information PII policy. The full potential of our employees and building Infosys reputation to make it the most respected company in the world.
Security is a war that must be won at all costs. The correct answer is 2. It is a moral right to be left alone.
Earlier chapters introduced the Institute of Medicine IOM committees conceptualization of health database organizations HDOs outlined their presumed benefits listed potential users and uses and examined issues related to the disclosure of descriptive and evaluative data on health care providers institutions agencies practitioners and similar entities. It is most easily obtained on the. Fathers age is three years more than three times the sons age.
Supreme Court has found that US. Our view in this chapter is that the conceptualand in part legalfoundations. Its very convenient after all.
Find the distance when they meet from starting point. Today individuals can achieve any level of privacy that is desired. Proliferation of networks and the Internet 4.
Constitution does not provide any right to privacy The US Supreme Court has found that US citizens have a right to privacy based upon the US Constitution The US. This policy addresses the issues relating to dealing of personal information collected by an organization. Which of the following isare true while applying bagging to regression trees.
X is a computer virus that made its appearance on March 26 th 1999 in the United States causing damage of more than 80 million dollars to American companies. Respect privacy and protect personal data. Infosys is the second-largest Indian IT company after Tata Consultancy Services by 2020 revenue figures and the 602nd largest.
Security is a war that must be won at all costs. Constitution does not provide any right to privacy.
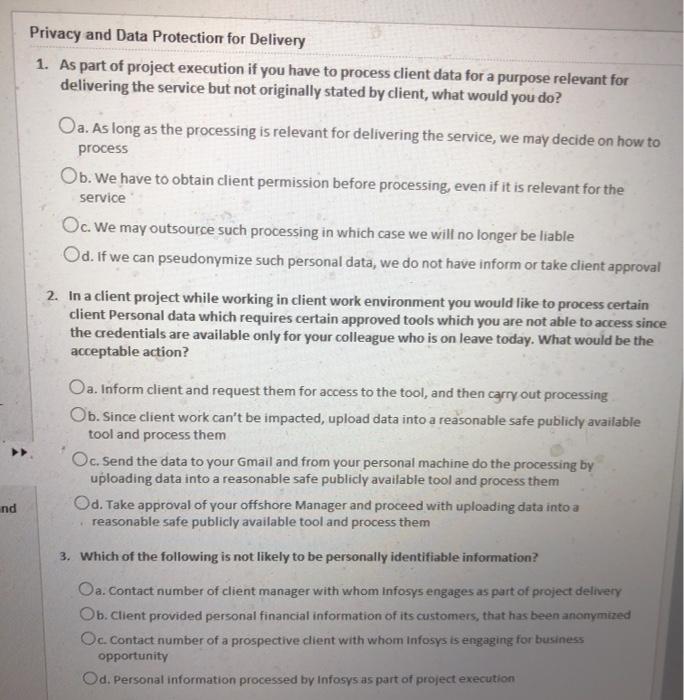
Solved Privacy And Data Protection For Delivery 1 As Part Chegg Com
(246).jpg)
Data Privacy Quiz Questions And Answers Proprofs Quiz
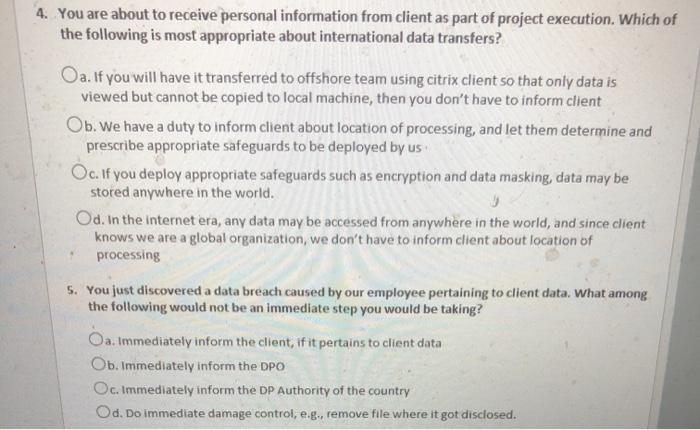
Solved Privacy And Data Protection For Delivery 1 As Part Chegg Com

20 Important Data Privacy Questions You Should Be Asking Now Cipher
0 Comments